
CL DATAPK provides crucial tools and services essential for maintaining asset security:
CL DATAPK was designed and developed with focus on discovering and preventing security incidents on the earliest stage possible. It is a cornerstone of the CyberLympha security platform - a comprehensive ICS security monitoring and analysis solution.
CL DATAPK is based on a robust composition of well-established IT security technologies, results of the contemporary studies in the field of ICS/OT security and deep practical expertise gained on commercial projects.
- benefits
- KEY FEATURES
- FUNCtION
- Monitor deviations from the reference system model and detect illegitimate changes in protected control systems
- Discover and manage assets, subject to critical vulnerabilities
- Detect exploitation attacks and monitor incident statuses from detection to remediation
- Collect and correlate security events from the assets
- Drive regulatory compliance with state and corporate policies regarding asset cybersecurity

- No agent software required for installation on the ICS components
- Minimum network load
- Various hardware support, incl. industrial appliances
- Several operation modes available for various ICS applications and desired interaction levels
- Local and centralized management
- Seamless integration with corporate security monitoring and/or SIEM systems

- Asset catalogue: automated ICS asset discovery and change management
- Security events management: collection, normalization and correlation
- Config management: collection and anomaly detection
- Compliance & security status control: vulnerability detection for ICS assets, compliance state analysis for governmental and corporate policies.

Solution architecture
The solution is based on a three-tier hierarchy of the CL DATAPK instances, providing all necessary services starting with network traffic collection and analysis and all the way to enterprise-level dashboards and reports. All components of the hierarchy reside in the Customer’s infrastructure and require no connection to the Internet or cloud-based services.
CL DATAPK can operate in observation mode, eliminating any possibility of traffic exchange with the protected assets, or query mode that allows bidirectional traffic exchange
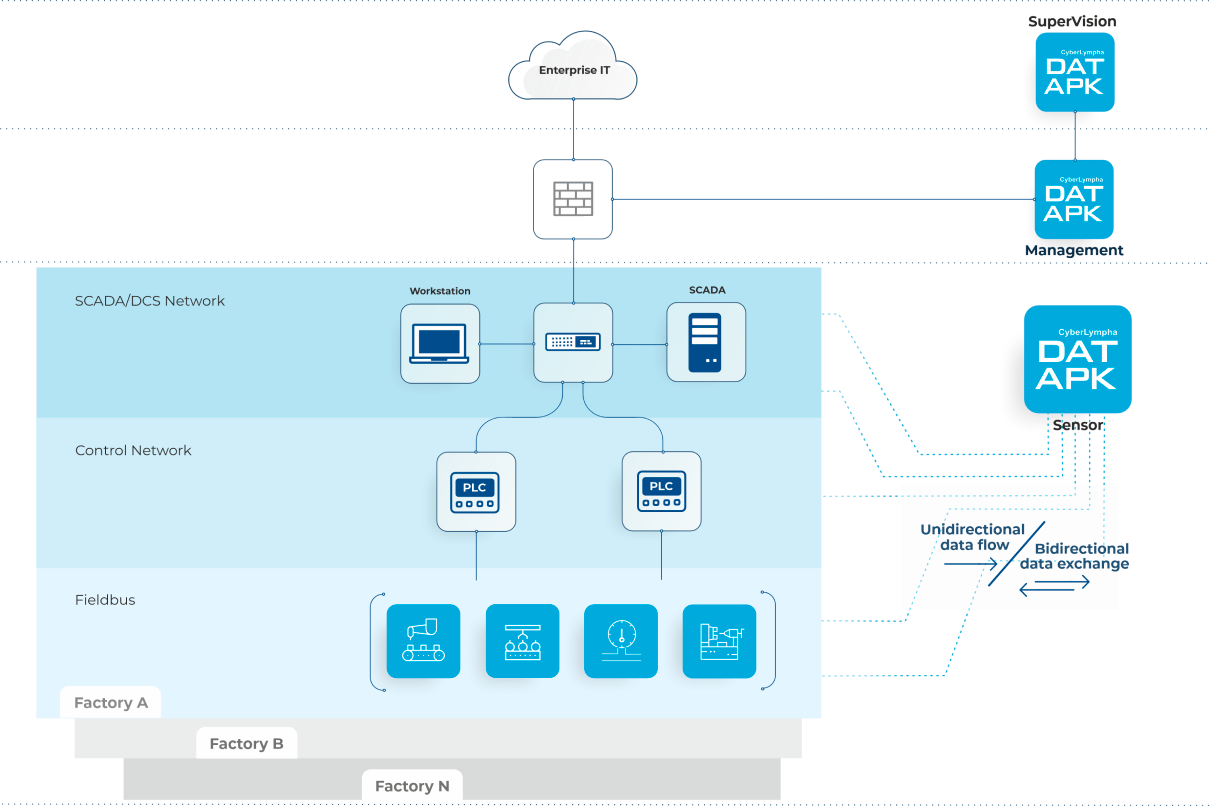
- Enterprise-level asset security status visualization based on the data collected from all underlying CL DATAPK Sensor and Management instances
- Enterprise-level security incident reporting
- Centralized management for the deployed CL DATAPK hierarchy
- Centralized update management for the CL DATAPK expert packages and software
- Integration with adjacent security solutions
- Data collection from the underlying CL DATAPK Sensors
- Asset catalogue and data flows management
- Automated topology visualization based on detected data flows
- Asset configurations management and compliance control
- Security assessments and status control for compliance with the implemented security policy
- Security events processing and management
- Security incident generation based on correlation of the events received from multiple sources
- Alerts via email service and SCADA integration
- ICS assets detection
- ICS data flows detection
- Network-based attacks detection
- Protocol-specific commands and parameters detection and validation
- Security events collection, registration and pre-processing
- Asset configurations and inventory information collection
Extensive configuration mechanisms built into the solution ensure compatibility with any ICS that is operated by the Customer. Using configuration to adjust CL DATAPK rather than modifying product code streamlines solution adaptation to protected assets.
CL DATAPK implements agentless interaction based on request-response mechanisms using standard and vendor-specific protocols, supported by the protected assets. Excluding agent software from the interaction process minimizes additional load on the assets’ processing power and nullifies the impact on ICS operation.
The tiered hierarchical architecture of the CL DATAPK provides a reliable foundation for building scalable security monitoring systems while maintaining single point of control and management. Flexible data exchange scheduling allows CL DATAPK to utilize existing WAN channels, including low throughput links, without impacting WAN operation.
The evolution of industrial control systems has led to extreme increase in efficiency and cost savings across all industries, but also brought the end to the concept of an air-gapped industrial and critical infractructure. Adopting comprehensive IoT technologies and converging IT and OT infrastructures brings risk management to the spotlight.
Secure your industrial assets with a comprehensive solution, delivering constant security monitoring for Enterprise OT infrastructure, IoT, Industrial Iot and other types of industrial control systems, and minimize the attack surface and vectors threatening the enterprise.


